Class 9 Cyber Olympiad - Sample question paper 05
Posted by Olympiad Tester on
Q) Examine the following CSS code:
#header {
background-color: #3498db;
color: #ffffff;
padding: 10px;
text-align: center;
}
What styling is applied to the element with the ID "header"?
A. Blue background, white text, 10px padding, centered text
B. White background, blue text, 10px padding, centered text
C. Blue background, black text, 20px padding, left-aligned text
D. Transparent background, red text, no padding, justified text
Answer: A. Blue background, white text, 10px padding, centered text
Explanation: The CSS code styles the element with the ID "header" by giving it a blue background, white text, 10px padding, and centering the text within the element.
Q) Analyze the following HTML code:
<div id="container">
<p class="intro">Welcome to the website</p>
<ul>
<li>Home</li>
<li>About</li>
<li>Contact</li>
</ul>
</div>
What is the purpose of the provided HTML code?
A. Displaying a list of items with links
B. Defining a container with an ID of "container"
C. Setting the background color of the page
D. Creating an image gallery
Answer: B. Defining a container with an ID of "container"
Explanation: The provided HTML code defines a <div> element with an ID of "container" and includes a paragraph and an unordered list inside it. The main purpose is to create a container with a specific ID.
Q) Raj is troubleshooting network connectivity issues on a Windows computer. He suspects a problem with the DNS configuration. Which command-line tool can he use to manually resolve domain names to IP addresses?
A. ipconfig
B. nslookup
C. netstat
D. tracert
Answer: B. nslookup
Explanation: nslookup is a command-line tool used to query Domain Name System (DNS) servers to obtain domain name or IP address mapping, helping in troubleshooting DNS-related issues.
Q) Maya wants to configure a secure wireless network on her Windows 10 laptop. Which protocol provides a more secure alternative to WPA2 for encrypting Wi-Fi traffic?
A. WEP
B. WPA
C. WPA3
D. TKIP
Answer: C. WPA3
Explanation: WPA3 (Wi-Fi Protected Access 3) is the latest Wi-Fi security protocol, providing improved encryption and security features over its predecessor, WPA2.
Q) Sanjay needs to share a large file with his colleague over the network. Which built-in Windows feature allows him to create a shared folder with specific permissions for his colleague to access the file?
A. HomeGroup
B. OneDrive
C. Windows Remote Assistance
D. Shared Folders (File Sharing)
Answer: D. Shared Folders (File Sharing)
Explanation: Shared Folders (File Sharing) in Windows allows users to share folders on the network with specific permissions, controlling who can access and modify the shared files.
Q) Which of the following statements is CORRECT about the <tbody> tag of <table> tag in HTML?
A. It is used to group the body content in an HTML table.
B. It is used in conjunction with the <thead> and <tfoot> elements.
C. It allows the web browsers to enable scrolling of the table body independently of the content in header and footer part.
D. All of these
Answer: D. All of these
Explanation: The <tbody> tag is used to group the body content of an HTML table. It is often used in conjunction with <thead> and <tfoot> elements. Additionally, it allows web browsers to enable scrolling of the table body independently of the content in the header and footer parts.
Q) Review the following JavaScript code:
function findMaximum(numbers) {
let max = numbers[0];
for (let i = 1; i < numbers.length; i++) {
if (numbers[i] > max) {
max = numbers[i];
}
}
return max;
}
const numbersArray = [8, 3, 11, 5, 7];
const maximumValue = findMaximum(numbersArray);
console.log(maximumValue);
What will be the output of the above code?
A. 8
B. 11
C. 7
D. 3
Answer: B. 11
Explanation: The JavaScript code defines a function findMaximum that finds and returns the maximum value in an array. The function is then called with an array of numbers, and the result is logged to the console.
Q) Nisha wants to encrypt sensitive data on her USB drive to prevent unauthorized access. Which Windows feature provides full-disk encryption and is suitable for securing removable drives?
A. Windows Defender Antivirus
B. BitLocker To Go
C. AppLocker
D. Credential Guard
Answer: B. BitLocker To Go
Explanation: BitLocker To Go is an extension of BitLocker that provides encryption for removable drives such as USB flash drives. It ensures that the data on the drive remains secure even if the drive is lost or stolen.
Q) Arjun is working on a shared network folder, and he wants to ensure that only authorized users can access specific files. Which Windows feature allows him to set detailed permissions for individual users and groups?
A. File History
B. Windows Defender Firewall
C. BitLocker Encryption
D. NTFS Permissions
Answer: D. NTFS Permissions
Explanation: NTFS (New Technology File System) provides advanced file and folder permissions, allowing users like Arjun to control access at a granular level, specifying who can read, write, or execute files.
Q) Priya wants to protect her computer from malware and unauthorized access. Which Windows feature allows her to create a virtual secure environment for running potentially harmful applications?
A. Windows Firewall
B. BitLocker
C. Windows Defender
D. Windows Sandbox
Answer: D. Windows Sandbox
Explanation: Windows Sandbox is a feature in Windows 10 that provides a secure and isolated environment for testing potentially harmful applications without affecting the main system.
Q) Ravi is experiencing slow performance on his computer, and he suspects it might be due to unnecessary startup programs. Which Windows utility can he use to manage and disable startup programs?
A. Task Manager
B. Control Panel
C. Disk Cleanup
D. System Configuration (msconfig)
Answer: D. System Configuration (msconfig)
Explanation: System Configuration allows users to manage startup programs. By disabling unnecessary programs, Ravi can potentially improve the computer's performance.
Q) What would be the output of the given flowchart?
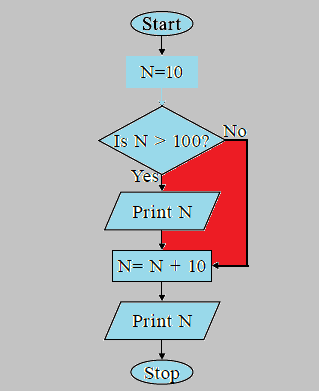
A. 20
B. 10
C. 11
D. 12
Answer: A. 20
Q) In multimedia, the horizontal movement of a camera to create the feeling of motion and speed without blurring the subject in a scene is known as _____________.
A. Morphing
B. Panning
C. Trimming
D. Framing
Answer: B. Panning
Explanation: Panning is a camera technique where the camera rotates horizontally to follow a moving subject or create a sense of motion.
Q) Kusum has installed a program, but the program caused Windows 7 to behave unresponsively. She uninstalled the program, but uninstalling did not fix the problem. Which of the following features will allow her to restore her computer’s settings to an earlier date when everything worked correctly?
A. System Restore
B. Disk Cleanup
C. Windows Update
D. Task Manager
Answer: A. System Restore
Explanation: System Restore is a feature in Windows that allows users to revert their computer's state to a previous point in time, known as a restore point. This can be helpful in fixing issues caused by recent changes, such as software installations.
Q) High-definition television (HDTV) display is an example of __________ operating system.
A. Real line
B. Real time
C. Integrity
D. Triggered
Answer: B. Real time
Explanation: The term "Real time" in this context likely refers to the fact that an HDTV system operates in real-time, providing a high-quality display without delays or buffering.
